As I mentioned in the past, I taught a Graduate level Risk Management and Incident response course. In my first term, I was literally hired three days before the term started. The grad class was new, with no framework or anything else to build off of, and I had to build it on the fly.
So, I went with what I learned in grad school elsewhere, which was the NIST documentation. During my first term teaching the class, I kept telling myself there must be something better. NIST SP 800-53 and the related documents have been around for a while, yet we still see breaches. It builds a framework around an organization, but something is missing. With the frameworks in place, breaches still happen and missing ways to help prioritize objectives.
Driving home after teaching class one night, I heard an interview with Jack Jones talking about Factor Analysis in Information Risk (FAIR). It made sense, and FAIR can tie actual monetary loss to things. So, I got a copy of the book but didn’t change the class in the middle of the term; I just waited for the next term the class was offered (it was only offered once a year).
When going through “Measuring and Managing Information Risk: A FAIR approach” by Jack Freund and Jack Jones, the book mentioned Threat intelligence several times, asking the Threat Intelligence experts, working with threat intelligence vendors, etc. And that part spoke to me too. Using the FAIR framework creates better planning/requirements and direction steps to speak to the threats a company faces.
In FAIR, threats don’t mean all the uses that we have in IT/Cyber Security, which boils down to speaking to an adverse event or action when something is exploited or compromised. In FAIR, a Threat is someone or something that can take independent action against an asset in a way that changes value. That made sense, too; it gave better, tighter definitions to work with.
As I read and thought more about FAIR, cybersecurity, and Threat Intelligence, I realized that Risk and Incident Response are two sides of the same coin. More or less. The Risk Management side is the expected annualized loss based on things happening. The Incident Response side is how an organization responds to materialized risk, or what the company does when the risk actually happens. And I thought about how Threat Intelligence plays into both Risk and Incident Response.
And while staring at the FAIR Framework, I came up with the below image. It is a modified version of the framework applied to areas of influence I see belonging in whole or in part to Threat Intelligence / Cyber Threat Intelligence showing the highlighted sections:
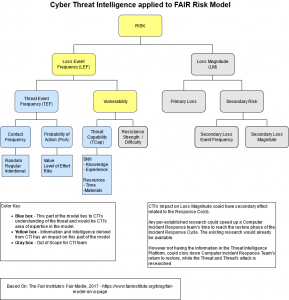
I’ll walk through the different parts and how I see Threat Intelligence’s role in each in future posts. They’re probably going to be mixed in with other things, but I’ll have a link page like I did the Building an OSINT box series that links to each part in order.
